🎯 Why Use a Cybersecurity Quiz in Your Business?
Cybersecurity quizzes transform your employees into the first line of defense against cyber threats. This guide shows you how to deploy interactive training that reduces phishing email clicks by 70% and improves security best practice retention by 80%.
What this guide contains:
- Understanding cybersecurity challenges: ransomware, phishing, data breaches, and human error
- Test your knowledge with 5 interactive quizzes created on Drag’n Survey
- Discover best practices: ongoing training, security policies, and essential tools
- Take action with ready-to-use quiz templates to train your teams
⚠️ Key figure: 95% of cybersecurity incidents in business involve human error. Training your teams is your best security investment.
In 2026, cybersecurity in business is no longer optional—it’s a vital necessity. Every day, thousands of organizations worldwide experience cyberattacks that can paralyze their operations, compromise sensitive data, and damage their reputation. The question is no longer whether your business will be targeted, but when.
Faced with this reality, raising awareness among your employees becomes your first line of defense. That’s why we’ve developed an innovative approach: interactive cybersecurity quizzes that transform training into an engaging experience. Because learning through engagement means learning for the long term.
>> Create a cybersecurity quiz with Drag’n Survey, click here

Cybersecurity Challenges for Business in 2026
Before diving into the interactive quizzes, let’s take a moment to understand the scope of the challenge. Cybersecurity challenges have evolved radically in recent years, and no organization is immune. Here’s what the latest studies reveal about cyber threats.
A Threat Affecting All Businesses
Cybersecurity challenges now affect all businesses, regardless of their size. The figures are unequivocal: 54% of international companies experienced at least one cyberattack in 2024, with an average cost of 60,000 dollars for SMEs. Even more alarming, 60% of small businesses that fall victim to a major attack go out of business within six months.
Increasingly Sophisticated Attacks
Ransomware now represents the most critical threat, with an attack every 11 seconds worldwide. But cybersecurity challenges extend far beyond just ransomware: phishing, data breaches, industrial espionage, sabotage… Attack vectors are multiplying and becoming increasingly sophisticated.
The Human Factor: Your Greatest Vulnerability
The human factor remains the weakest link: 95% of cybersecurity incidents are linked to human error. An unfortunate click on a fraudulent email, a weak password, an infected USB drive plugged in by mistake… Your employees are simultaneously your greatest vulnerability and your best protection.
Interactive Training for All Your Employees
This is precisely why we’re offering this unique training article. Through several cybersecurity quizzes created with Drag’n Survey, you’ll be able to assess your knowledge, identify your areas of weakness, and acquire the essential reflexes to protect your business. Each quiz addresses a specific cybersecurity challenge in business, with concrete cases and detailed explanations.
What is a Cybersecurity Quiz?
A cybersecurity quiz is an interactive training tool that helps assess and improve employees’ knowledge of digital threats in business. Unlike traditional training, quizzes transform learning into an engaging and measurable experience.
The 5 Components of an Effective Cybersecurity Quiz
A cybersecurity quiz in business typically covers 5 essential areas:
- Ransomware: recognizing infection attempts and protection reflexes
- Phishing: identifying fraudulent emails and phishing techniques
- Password management: creating strong passwords and using multi-factor authentication
- Data protection: secure handling of sensitive information
- Human errors: risky behaviors and daily best practices
How Does a Cybersecurity Quiz Work in Practice?
The principle is simple but remarkably effective. Employees answer a series of 5 to 15 questions based on real situations they might encounter in their daily work: a suspicious email in their inbox, an unusual request from a colleague, a USB drive found on the premises, etc.
Each answer is followed by a detailed explanation that helps understand why a choice is correct or incorrect. It’s this combination of scenario-based learning + immediate feedback that makes cybersecurity quizzes so effective at reinforcing good reflexes.
Why Are Quizzes More Effective Than Traditional Training?
The figures speak for themselves. According to cognitive science studies:
- We retain 10% of what we read (documentation, procedures)
- We retain 20% of what we hear (presentation, webinar)
- We retain 80% of what we actively experience (interactive quiz)
Cybersecurity quizzes actively engage the brain in a process of reflection, decision-making, and memorization. The gamified aspect with scoring improves team engagement, who perceive training as a challenge rather than a constraint.
💡 Good to know: A 10-minute cybersecurity quiz conducted each month is more effective than a 2-hour training session conducted once a year. Spaced repetition is the key to lasting memorization.
Cybersecurity Quiz: For Whom and How Often?
Contrary to popular belief, cybersecurity in business doesn’t only concern IT teams. All employees are involved:
- Sales teams: exposed to targeted spear phishing and customer data leaks
- Human resources: handle sensitive personal data
- Executive management: prime targets for sophisticated attacks
- Support teams: first responders to security incidents
- Remote workers: use potentially unsecured connections
Recommended frequency: Organize an initial diagnostic cybersecurity quiz, then monthly or quarterly thematic sessions. This regularity helps maintain a high level of vigilance and update knowledge in response to emerging threats.

Measurable Benefits of a Cybersecurity Quiz Program
Companies that deploy regular cybersecurity quizzes observe:
- A 70% reduction in clicks on phishing emails during penetration tests
- An 85% improvement in two-factor authentication adoption
- A 60% decrease in incidents related to human errors
- A 50% reduced response time when an incident is detected by an employee
- A security culture where employees become proactive actors rather than weak links
More than just an assessment tool, cybersecurity quizzes become a strategic lever to transform your employees into the first line of defense against cyber threats.
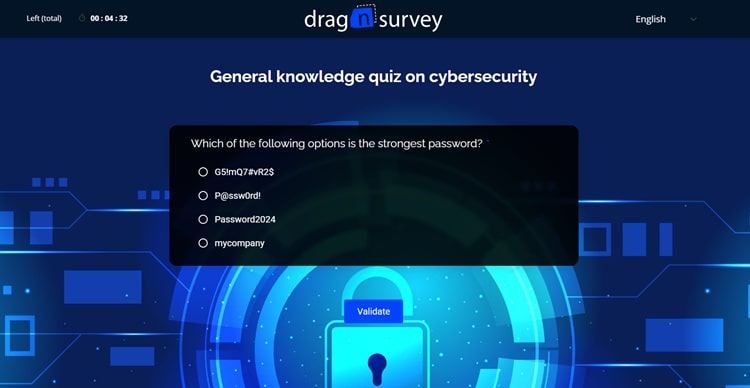
Cybersecurity Quiz: Assess Your Protection Level
Now that you understand the challenges, it’s time to take action! But before diving into the details of each threat, let’s start by assessing your current level of cybersecurity awareness in business.
Why This Cybersecurity Quiz is Essential
This diagnostic quiz will help you quickly identify your strengths and areas for improvement in cybersecurity. In just a few minutes, you’ll get a clear picture of your level of preparedness against the most common cyber threats. Whether you’re a beginner or already aware, this test will help you become conscious of the reflexes you need to adopt daily.
How This Cybersecurity Quiz Works
This general cybersecurity quiz includes 5 questions covering different aspects of IT security in business: recognizing fraudulent emails, password management, risky behaviors, security reflexes, etc. Each question is based on concrete situations you might encounter in your daily work.
Complete Your Cybersecurity Diagnostic
Take 5 minutes to answer this quiz honestly. There are no wrong answers: the goal is to identify your training needs to better protect yourself and your business.
Click on the image to access the general cybersecurity knowledge quiz
Cybersecurity Challenges for Business
Have you completed your general diagnostic? Perfect! It’s now time to deepen your understanding of the four major cybersecurity challenges in business. Each challenge represents a concrete risk that can impact your organization daily. For each one, we offer a specialized cybersecurity quiz that will help you master best practices and adopt appropriate security reflexes.
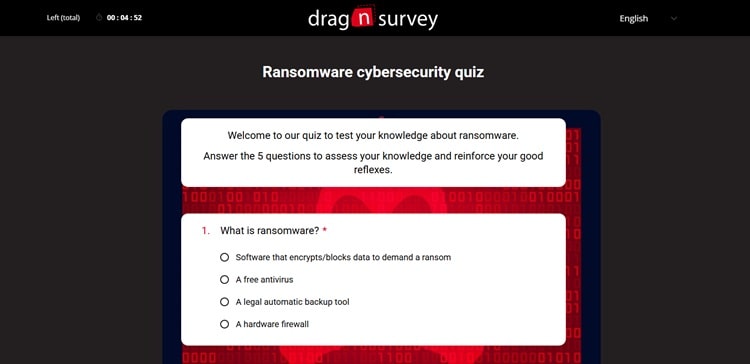
Challenge #1: Ransomware
First major challenge: ransomware. This threat regularly makes headlines, and for good reason. Ransomware attacks can bring an entire company to its knees in just a few hours. Understanding how they work and knowing how to protect against them has become essential for all employees.
What is Ransomware and Why is it So Dangerous?
Ransomware, or rançongiciels in French, represents one of the most devastating threats to businesses. These are malicious software programs that encrypt all your data and systems, making them completely inaccessible. Cybercriminals then demand payment of a ransom, usually in cryptocurrency, to give you back access to your files.
The impact on cybersecurity in business is catastrophic: complete shutdown of operations, loss of critical data, reputational damage, and remediation costs running into tens or hundreds of thousands of dollars. In USA, the average cost of a ransomware attack reaches 300,000 dollars for SMEs, not counting lost revenue.
How Do Ransomware Infiltrate Your Business?
Ransomware generally enter your system through three main entry points: phishing emails containing infected attachments, exploitation of vulnerabilities in non-updated software, or via poorly secured RDP (Remote Desktop Protocol) access. A single employee error can be enough to compromise your entire network.
Warning Signs to Watch For
Certain signals should immediately alert you: unexplained computer slowdown, inability to open certain files, appearance of strange file extensions (.locked, .encrypted, .crypted), unusual network activity, or suspicious requests for administrator access. The earlier you detect the attack, the better your chances of limiting the damage.
Best Practices to Protect Yourself
Protection against ransomware relies on several pillars: regular backups disconnected from the network (3-2-1 rule), systematic updating of your software and operating systems, use of high-performance antivirus and anti-malware solutions, restriction of administrator rights, and above all training your teams to recognize infection attempts.
Test Your Knowledge of Ransomware
Are you capable of recognizing a ransomware attack attempt? Do you know how to react in case of infection? This specialized cybersecurity quiz will put you in real situations to test your reflexes against this threat.
Click on the image to access the ransomware cybersecurity quiz
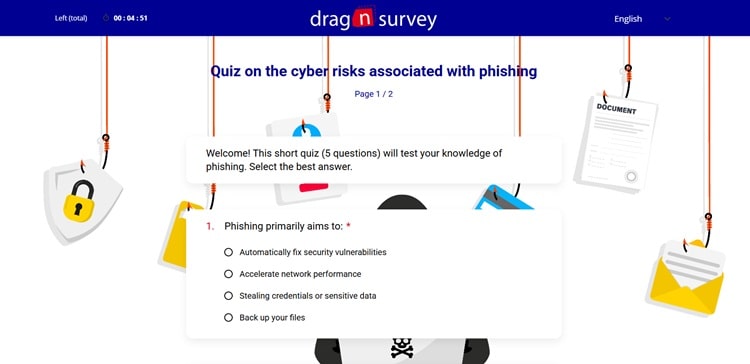
Challenge #2: Phishing
Now let’s move on to the most widespread threat in business: phishing. If you use a professional email account, you’ve certainly already received one. The problem is that some phishing attempts have become so sophisticated that they can fool even the most vigilant employees.
Phishing: The Most Widespread Attack Technique
Phishing, or hameçonnage, is a social engineering technique that aims to trick you into disclosing confidential information: credentials, passwords, banking details, strategic information, etc. Cybercriminals pose as trusted entities (bank, government, colleague, supplier) to manipulate you.
This threat represents one of the most critical cybersecurity challenges because it directly targets the human factor. According to statistics, 91% of cyberattacks begin with a phishing email. In business, the consequences can be dramatic: compromised professional accounts, customer data theft, fund diversion, or entry point for more sophisticated attacks like ransomware.
Different Forms of Phishing
Phishing isn’t limited to emails. Smishing uses SMS, vishing operates through fraudulent phone calls, and spear phishing specifically targets identified individuals with ultra-personalized messages. Attackers have become experts in the art of manipulation, and their messages increasingly credible, perfectly imitating legitimate communications.
How to Recognize a Phishing Attempt?
Several clues should raise your suspicion: artificial sense of urgency (your account will be blocked in 24 hours), spelling or grammar mistakes, a sender email address that doesn’t exactly match the official domain (banque-fr.com instead of banque.fr), suspicious links (hover without clicking to see the real destination), unusual requests for confidential information, or unexpected attachments.
Anti-Phishing Reflexes to Adopt
Never click on a suspicious link. When in doubt, contact the company or person directly through another channel (phone, visiting the official site). Always verify the complete email address of the sender. Never communicate your credentials or passwords by email. Immediately report any phishing attempt to your IT department. And above all: take time to think before acting, even under pressure.
Can You Detect the Traps?
This cybersecurity quiz will present you with real examples of phishing emails, some obvious, others particularly sophisticated. Your mission: identify them and understand the warning signs.
Click on the image to access the phishing cybersecurity quiz
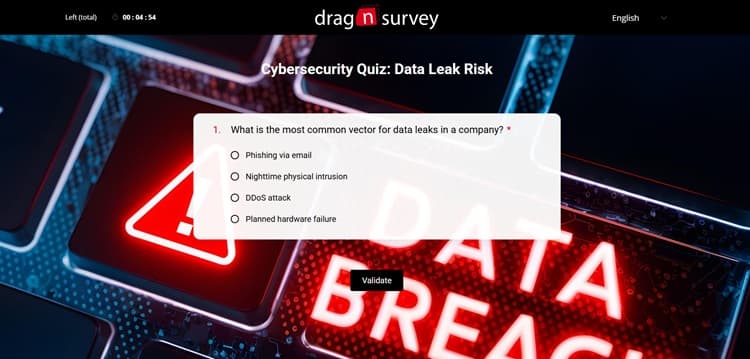
Challenge #3: Data Breaches
Third major challenge: protecting your sensitive data. In the era of massive digitalization, data breaches have become a nightmare for businesses. A single breach can have disastrous financial and reputational consequences, not to mention legal sanctions.
When Sensitive Information Falls into the Wrong Hands
A data breach occurs when confidential information from your business is exposed, stolen, or disclosed to unauthorized persons. This data can include customer information (names, emails, banking details), trade secrets, commercial strategies, health data, or information about your employees.
The consequences for cybersecurity in business are multiple and serious: loss of customer and partner trust, damage to brand image, risk of lawsuits, and malicious exploitation of stolen data. On average, a data breach costs a company $4.45 million globally.
Main Causes of Data Breaches
Data breaches don’t always result from sophisticated attacks. They can be caused by: a successful cyberattack (ransomware, hacking), human error (sending an email to the wrong recipient, losing an unencrypted laptop), poor system configuration (publicly accessible database), a malicious employee, or vulnerabilities in third-party applications you use.
The Most Sensitive Data to Protect
Certain data requires heightened vigilance: your customers’ and prospects’ personal data, financial and banking information, manufacturing secrets and intellectual property, contracts and confidentiality agreements, health data, credentials and passwords, as well as any strategic information concerning your business. Clearly identify what your critical data is and implement reinforced protections.
How to Prevent Data Breaches
Prevention relies on several concrete actions: classify your data according to their level of sensitivity, encrypt sensitive data in transit and at rest, limit access according to the principle of least privilege, monitor abnormal activities on your systems, train your employees in best practices, conduct regular security audits, and have an incident response plan.
Are You Vigilant About Data Protection?
This cybersecurity quiz will confront you with real situations where sensitive data is at stake. Will you be able to identify the risks and adopt the right behaviors to protect your business’s information?
Click on the image to access the data breach cybersecurity quiz
Challenge #4: Human Error
Last but not least challenge: human error. We often say that the weak link in cybersecurity sits between the chair and the keyboard. This statement may seem harsh, but it reflects an undeniable reality: even the best security systems can be bypassed by a simple handling error.
The Weak Link in the Security Chain
Human error paradoxically constitutes one of the most critical and most neglected cybersecurity challenges. You can invest millions in the best firewalls, antivirus, and intrusion detection systems, but a single careless click from an employee can destroy all these efforts. The statistics speak for themselves: 95% of cybersecurity incidents in business involve human error.
This reality doesn’t mean your employees are incompetent or negligent. On the contrary, most errors come from conscientious people who don’t realize they’re committing a security fault. This is precisely why training and awareness-raising are essential: you can’t avoid what you don’t know.
Most Common Human Errors
Among the most common errors, we find: using weak passwords or reusing them across multiple accounts, clicking on suspicious links or attachments, sharing sensitive information through unsecured channels (personal email, unencrypted messaging), connecting to public WiFi without VPN, forgetting to lock their workstation when stepping away, installing unauthorized software, or not following security procedures for convenience or to save time.
Why Do We Commit These Errors?
Several psychological and organizational factors explain these risky behaviors. Cognitive overload and workplace stress reduce our vigilance. Overconfidence makes us underestimate risks (“it won’t happen to me”). Time pressure pushes us to take shortcuts. Lack of training leaves us unaware of certain dangers. And sometimes, overly restrictive security procedures encourage bypassing them rather than following them.
Creating a Collective Security Culture
Fighting human error doesn’t involve blame but creating a true cybersecurity culture in business. This implies: regularly training all employees (not just the IT team), encouraging incident reporting without fear of sanctions, designing ergonomic and realistic security procedures, regularly communicating about current threats, celebrating good behaviors, and above all accepting that error is human while implementing safeguards to limit their impact.
Best Practices to Automate
Certain reflexes should become automatic: always verify the sender before opening an attachment, hover over links before clicking, systematically lock your workstation when stepping away, use a password manager, activate two-factor authentication wherever possible, never share your credentials, immediately report any suspicious behavior, and always ask yourself “is this action safe?” before acting.
Measure Your Daily Vigilance
This final cybersecurity quiz will put you in everyday situations where errors can easily slip in. The goal: identify your own blind spots and develop permanent vigilance in your daily use of digital tools.
Click on the image to access the cybersecurity quiz on risks related to human error
You’ve now explored the four major cybersecurity challenges for business. Each cybersecurity quiz has helped you deepen a specific aspect and identify your areas for improvement. But knowledge isn’t enough: you now need to take action and concretely implement these best practices in your organization.
Cybersecurity Best Practices in Business
You now have a thorough understanding of the four major cybersecurity challenges and have tested your knowledge through our various quizzes. It’s time to move to the next step: transforming this knowledge into concrete action within your organization. Implementing cybersecurity in business isn’t limited to installing protection software—it’s above all a comprehensive approach involving your teams, your processes, and your tools.
Train Your Teams with Cybersecurity Quizzes
Knowledge without action protects no one. Now that you understand the challenges and have tested your own knowledge, the question is: how do you transmit this cybersecurity culture to all your employees? The answer lies in a continuous, engaging, and measurable training approach.
Continuous Training: Pillar of Cybersecurity in Business
Raising awareness and training your employees constitutes the first line of defense against cyber threats. Training your teams isn’t an option, it’s an absolute necessity. But beware: a single training session during onboarding isn’t enough. Threats constantly evolve, and knowledge erodes quickly without regular practice.
Why Are Cybersecurity Quizzes So Effective?
Cybersecurity quizzes represent a particularly effective training method for several reasons. First, they’re engaging and playful, which encourages adoption from employees often reluctant to traditional training perceived as restrictive. Next, they enable immediate assessment of knowledge and precisely identify each participant’s gaps. Finally, the interactive format significantly improves information retention: we retain 10% of what we read, 20% of what we hear, but 80% of what we actively experience.
Quizzes also offer the advantage of being easily deployable at scale, customizable according to functions and risk levels, and measurable to track your teams’ progress over time. You can thus adapt your training strategy based on observed results.
Implementing a Quiz-Based Training Program
To effectively deploy cybersecurity quizzes in your business, start with a general diagnostic quiz to assess your employees’ baseline level. Then organize monthly or quarterly thematic sessions on specific topics: ransomware, phishing, password management, data protection, etc. Vary formats with short quizzes (5 minutes) for regular reminders and in-depth quizzes (15-20 minutes) for comprehensive training.
Create different pathways adapted to roles: sales teams don’t have the same needs as IT or HR teams. Integrate practical cases based on real situations encountered in your industry sector. And above all, gamify the experience with scores, rankings, and why not rewards for the best results, while maintaining a benevolent approach focused on learning rather than punishment.
Create Your Own Training Quizzes with Drag’n Survey
Would you like to deploy a cybersecurity quiz training strategy in your business? Drag’n Survey offers all the necessary tools to create professional, engaging, and effective quizzes. Our platform allows you to easily design interactive surveys with automatic scoring, personalized feedback based on responses, and detailed dashboards to track your teams’ results.
You can create quizzes with different types of questions (multiple choice, true/false, scenarios), integrate images and videos to illustrate your scenarios, and fully customize the design with your company’s colors. Results are analyzed in real-time, allowing you to quickly identify employees requiring reinforced support and topics to deepen.
Policies and Procedures
Training your employees is essential, but that’s not enough. For cybersecurity to become a daily reality in your business, you must establish a clear framework that defines the rules of the game. This is where policies and procedures come in—the true safeguards of your organization.
Formalizing Your Cybersecurity Framework
Beyond training, cybersecurity in business requires a structured framework of clearly defined policies and procedures. These documents constitute the backbone of your security strategy and establish common rules understood and applied by everyone. Without this formal framework, even the best-trained employees can adopt risky behaviors simply through ignorance of the rules in force.
Essential Policies to Implement
Start by developing a comprehensive IT security policy that defines general principles, everyone’s responsibilities, and sanctions for non-compliance. This policy must be validated by management and communicated to all employees upon their arrival in the company.
Then develop a password management policy that imposes complexity criteria, a validity period, prohibition of reuse, and the obligation to use two-factor authentication on critical systems. Complete with an acceptable use policy that defines what is authorized or prohibited: personal use of professional equipment, accessible websites, software downloads, use of company WiFi, etc.
Don’t forget the data classification policy that establishes confidentiality levels (public, internal, confidential, secret) and handling rules for each level. Add an incident management policy that describes the procedure to follow in case of suspicion or detection of a cyberattack, with emergency contacts and priority actions.
Finally, create a remote work policy particularly crucial since the widespread adoption of teleworking, covering home network security, VPN use, physical equipment protection, and videoconferencing best practices.
Transforming Policies into Operational Procedures
Policies define the “what,” procedures explain the “how.” For each policy, develop detailed procedures, step by step, accessible and easy to follow. For example, create a suspicious email reporting procedure, a security incident declaration procedure, a data access request procedure, or an employee departure procedure including revocation of all their access.
These procedures should be written in clear language, without excessive technical jargon, and accompanied by screenshots or video tutorials when relevant. Make them easily accessible via your intranet or internal knowledge base, and ensure they’re kept up to date as your systems and threats evolve.
Bringing Your Security Policies to Life
A policy that stays in a drawer serves no purpose. Organize information sessions during each major update, integrate policy presentations into new hires’ onboarding process, and have all your employees sign a compliance commitment. Conduct regular audits to verify effective application of rules, and adapt your policies based on feedback and evolving risks.
Also remember that security policies must remain realistic and proportionate. Overly restrictive or inappropriate rules for daily work reality will be systematically bypassed, creating a false sense of security while actually weakening your protection.
Tools and Solutions
You’ve trained your teams, established your rules and procedures. It’s now time to equip your business with the right technological tools. Because while humans remain at the heart of cybersecurity, technical solutions constitute essential ramparts that automate and reinforce your protection.
Technologies Serving Your Cybersecurity
Cybersecurity best practices in business rest on three pillars: people (training), processes (policies and procedures), and technologies (tools and solutions). You’ve now worked on the first two pillars, let’s address the third. Technological tools don’t replace human vigilance, but they constitute indispensable shields and automate numerous protections.
Essential Protection Solutions
Professional antivirus and anti-malware: Choose enterprise-grade solutions with real-time protection, automatic updates, and centralized management. Free consumer-grade antivirus aren’t sufficient for a professional organization.
Next-generation firewall: Beyond simple port filtering, opt for firewalls that analyze traffic content, detect suspicious behaviors, and block malicious connections.
Backup and continuity solutions: Implement the 3-2-1 rule (3 copies of your data, on 2 different media, including 1 off-site). Automate your backups and regularly test your restoration procedures. An untested backup is a potentially unusable backup.
Enterprise password managers: Deploy a centralized solution that allows your employees to generate and store complex passwords without having to memorize them. Some solutions also offer secure sharing of credentials between teams.
VPN (Virtual Private Network): Essential for securing remote connections, especially for your teleworkers or traveling employees. VPN encrypts all traffic and protects against data interception on unsecured networks.
Email filtering solutions: Secure email gateways analyze your incoming emails to block spam, phishing, and malicious attachments before they reach your employees’ inboxes.
Intrusion detection and prevention systems (IDS/IPS): These tools monitor your network continuously to detect abnormal activities and can automatically block intrusion attempts.
Identity and access management solutions (IAM): To finely control who has access to what in your information system, with multi-factor authentication and centralized rights management.
| Solution Type | Primary Function | Threats Covered | Priority | Average Cost |
|---|---|---|---|---|
| Antivirus/Anti-malware | Detection and removal of malicious software | Ransomware, viruses, trojans, spyware | ⚠️ Essential | 50-150 dollars/workstation/year |
| Firewall | Filtering inbound/outbound network traffic | Intrusions, unauthorized access, DDoS attacks | ⚠️ Essential | 500-5,000 dollars/year |
| Backup Solution | Copy and restoration of critical data | Ransomware, data loss, hardware failures | ⚠️ Essential | 100-500 dollars/month |
| Password Manager | Secure creation and storage of credentials | Phishing, weak passwords, human errors | ⚡ Important | 3-10 dollars/user/month |
| Enterprise VPN | Encryption of remote connections | Data interception, espionage, public WiFi | ⚡ Important | 5-20 dollars/user/month |
| Email Filtering | Blocking malicious emails and spam | Phishing, spear phishing, infected attachments | ⚡ Important | 2-5 dollars/user/month |
| IDS/IPS | Detection and prevention of network intrusions | Advanced attacks, lateral movements, APT | ✓ Recommended | 1,000-10,000 dollars/year |
| IAM (Access Management) | Control of access rights and identities | Unauthorized access, internal data leaks | ✓ Recommended | 5-10 dollars/user/month |
| Training Platform (Drag’n Survey) | Continuous training through cybersecurity quizzes | All (prevention through human awareness) | ⚠️ Essential | Variable (free offer available) |
💡 Good to know: Technical solutions never replace human training. With 95% of incidents involving human error, investing in awareness-raising through cybersecurity quizzes is as essential as antivirus or firewall.
Drag’n Survey: An Ally for Your Cybersecurity
You might wonder what the connection is between an online survey platform and cybersecurity? The connection is threefold and essential.
First, continuous training: as we’ve seen, Drag’n Survey allows you to easily create and deploy cybersecurity quizzes to regularly train your teams. Our platform becomes your permanent awareness-raising tool, with the ability to schedule recurring training campaigns and track your employees’ skills development over time.
Second, measurement and audit: use Drag’n Survey to conduct internal surveys on security practices actually applied by your teams. Where do they really stand in applying your policies? What are the friction points? This valuable feedback will allow you to adjust your cybersecurity strategy to make it more effective and better accepted.
Building Your Security Ecosystem
The challenge isn’t to accumulate the maximum number of tools, but to build a coherent ecosystem adapted to your real needs. Start with the fundamentals (antivirus, firewall, backups), then progressively add protection layers according to your maturity level and resources. Ensure your different solutions communicate with each other and that you have a centralized view of your security posture.
And never forget: the best tools in the world are useless without trained and vigilant employees. This is why continuous training through cybersecurity quizzes remains your most profitable investment in IT security.
Cybersecurity Quiz: Take Action
You’ve discovered the four major cybersecurity challenges in business and tested your knowledge through our interactive quizzes. But the real question now is: what will you do with this knowledge? Cybersecurity isn’t a state you achieve once and for all—it’s a continuous process of vigilance and improvement.
Your Next Steps
This week: Share this article with your colleagues and encourage them to take the cybersecurity quizzes. Do a quick audit of your practices: password manager, backups, updates, two-factor authentication. Identify quick wins that can immediately improve your security.
This month: Create your own cybersecurity quizzes adapted to your context with Drag’n Survey. Plan regular awareness-raising sessions and begin formalizing your security policies. Don’t wait to be a victim of an attack to act.
This quarter: Measure your teams’ awareness level, evaluate your current security tools, and adjust your training strategy based on observed results.
Transform Your Organization with Drag’n Survey
With Drag’n Survey, quickly deploy a cybersecurity culture: ready-to-use templates, recurring training dispatch and progress tracking.
Cybersecurity Starts with You
Remember: 95% of incidents involve human error, but this also means that 95% of attacks can be prevented by well-trained employees. You have this power. Every action counts: verifying an email, hovering over a link, creating a strong password, installing an update.
FAQs on Cybersecurity in Business
What is a cybersecurity quiz?
A cybersecurity quiz is an interactive training tool that helps evaluate and improve employees’ knowledge about digital threats. It typically covers 5 key areas: ransomware, phishing, password management, data protection, and human error.
Why is corporate cybersecurity important even for small organizations?
Corporate cybersecurity is crucial for all organizations, regardless of their size. Cybercriminals particularly target SMEs because they generally have fewer protections than large companies while handling valuable sensitive data. In USA, the average cost of a cyberattack is $300,000 for SMEs. Even more alarming, 60% of small businesses that fall victim to a major attack go bankrupt within six months. Investing in cybersecurity is therefore not a luxury but a survival necessity.
How do I create an effective cybersecurity quiz to train my teams?
To create an effective cybersecurity quiz, start by identifying threats specific to your sector and the most frequent risky behaviors in your organization. Use a platform like Drag’n Survey to design surveys with 10 to 15 questions based on concrete situations that your employees might actually encounter. Incorporate different types of questions: multiple choice, true/false, and scenario-based situations with screenshots of phishing emails, for example. Add an automatic scoring system and most importantly, provide detailed explanations after each answer to transform the quiz into a genuine learning tool. Schedule regular sessions (monthly or quarterly) rather than a one-time training, as spaced repetition significantly improves information retention. Gamify the experience with leaderboards and rewards while maintaining a supportive approach focused on learning.
What are the main cybersecurity challenges that businesses must face?
Cybersecurity challenges for businesses revolve around four major threats. First, ransomware that encrypts your data and demands a ransom, with an attack every 11 seconds worldwide and an average cost of $1,200,000 for SMEs. Second, phishing, which represents the starting point of 91% of cyberattacks and aims to steal your credentials through psychological manipulation. Third, data breaches that expose confidential information. Fourth, human error, which constitutes the weak link since 95% of cybersecurity incidents involve human fault: clicking on a suspicious link, weak passwords, carelessness in sharing information. These four challenges are interconnected and require a comprehensive approach combining training, procedures, and technical tools.
What is the difference between a cybersecurity quiz and traditional IT security training?
A cybersecurity quiz stands out from traditional training through its interactive and engaging approach that promotes active learning. Unlike traditional training often perceived as long and boring, quizzes offer short sessions of 5 to 15 minutes easily integrated into daily work routines. The playful aspect with scoring and gamification significantly improves employee engagement: we retain 10% of what we read, 20% of what we hear, but 80% of what we actively experience. Quizzes also provide immediate knowledge assessment and precisely identify individual gaps, allowing for personalized training paths. They are easily deployable at scale, measurable to track progress, and can be repeated regularly without causing fatigue. Finally, quizzes allow testing of concrete and realistic situations, such as recognizing a real phishing email, which develops reflexes immediately applicable in daily work.
More abouit surveys:
Find form examples to use, click here
Best practices for creating a survey, click here
Find a European alternative to Alchemer, click here
Steps to succeed with a satisfaction survey, click here
The essential guide to creating a free survey, click here
Compare Drag’n Survey and SurveyMonkey features, click here
Differences between a tool like Typeform and Drag’n Survey, click here
Key differentiators between Microsoft Forms and Drag’n Survey, click here
Read the article:
French – quiz cybersécurité, click here
German – quiz zur Cybersicherheit, click here
Portuguese – quiz sobre segurança cibernética, click here
Polish – quiz dotyczący bezpieczeństwa w Internecie, click here